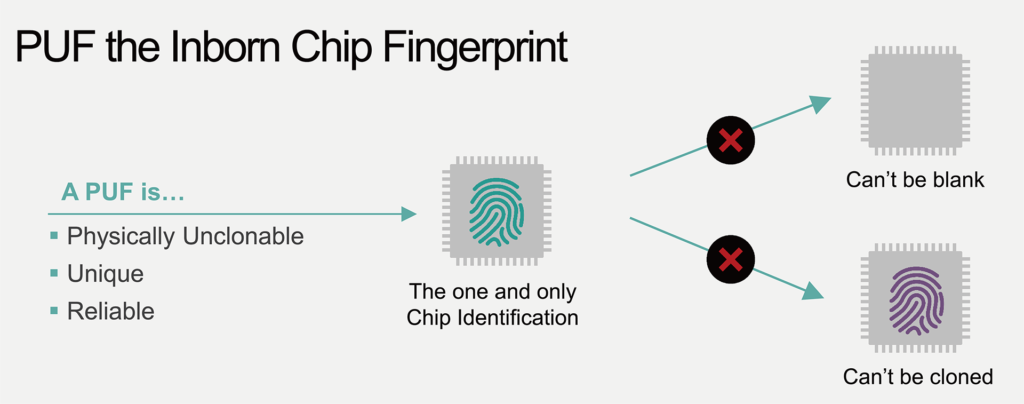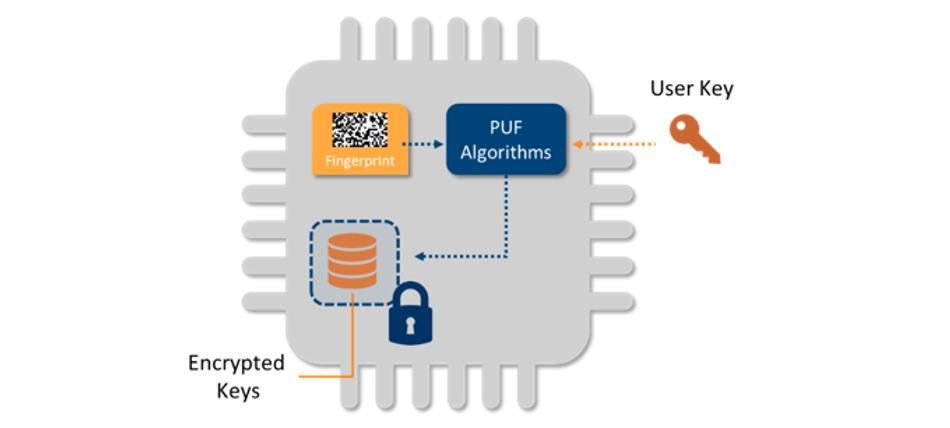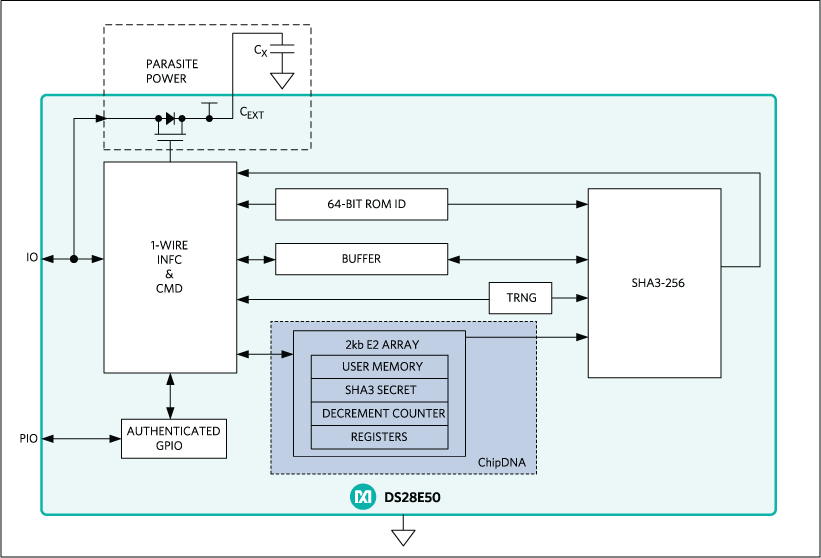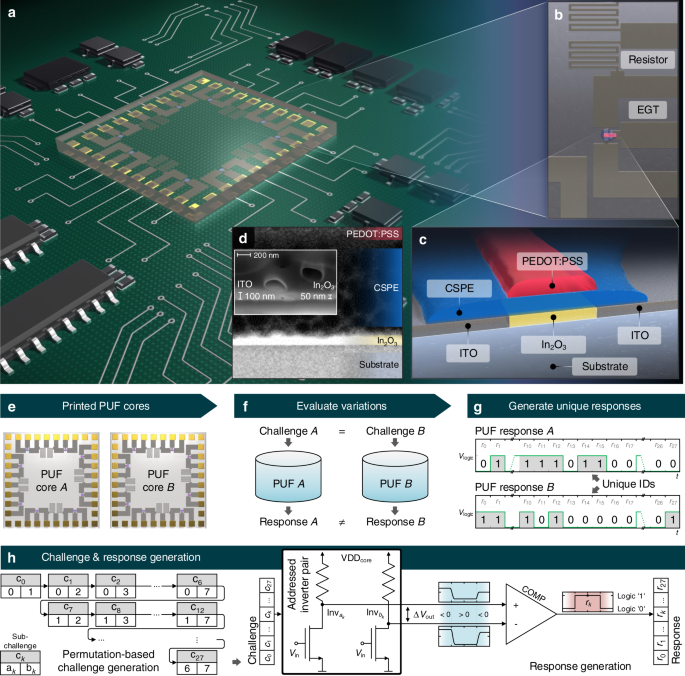
Hybrid low-voltage physical unclonable function based on inkjet-printed metal-oxide transistors | Nature Communications
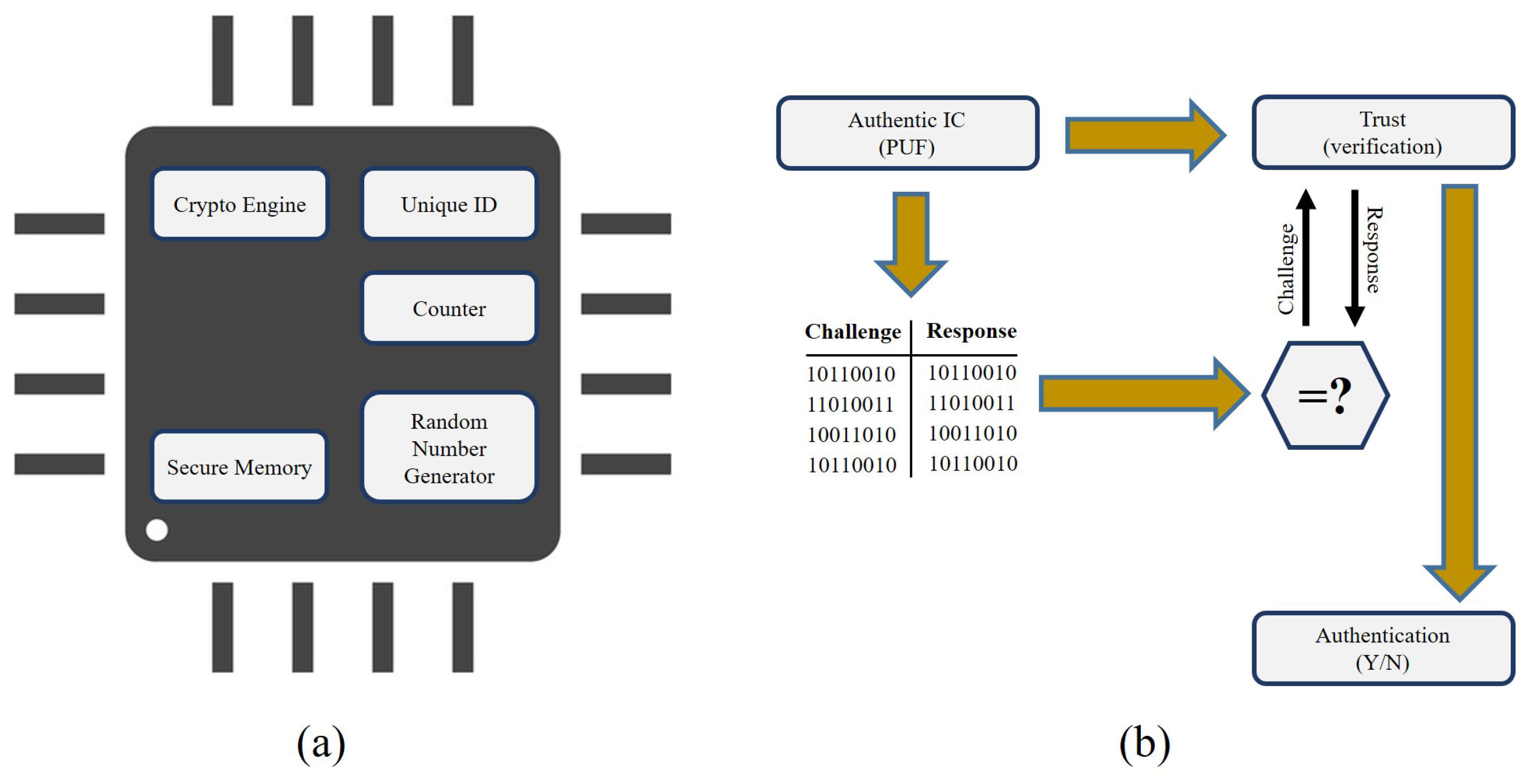
Sensors | Free Full-Text | Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy | HTML